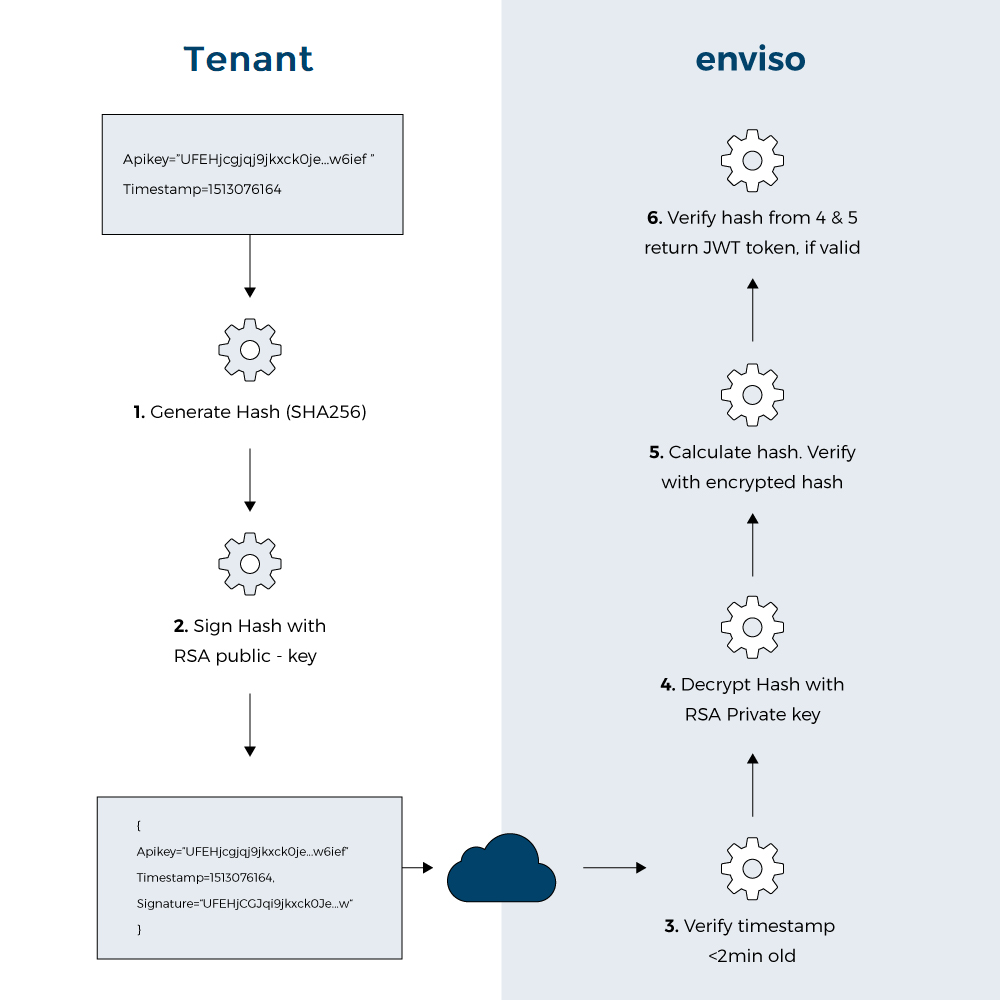
Procedure:
Concatenate the API key with the current timestamp in the format below: <<APIKEY>>_<<timestamp(yyyy'-'MM'-'ddTHH:mm:ss.fffZ)>>
Create a SHA256 hash of this value. Based on the hashed value, a digital signature will be created.
The combination of the created signature along with the provided API secret key will act as the digital signature of the call.
Send these values to the login action.
After successful validation, a JWT Access bearer token will be provided.
The validity of the JWT token is 1 hour. The parameter refreshToken allows you to extend the session by renewing the JWT token from the server-side before the existing token expires.
To make this process easier, a sample application is created which can be used to validate if the created signature is correct. It is also available on https://github.com/gantner-nv/EnvisoApiAuthentication
Example:
Assuming we have the following data
The hashed value of step 2 will be:
9952375a30708b46739986482303cae30ad51fc9a362b5794d298dfc22f7ec02
The signature of step 3 will be:
iMTchrTU9pMWFDRYQNCnUiD2ekDdCgp0ybN7xzvj9DLtceTFsF/kxzr9q5OnqP0quyt7OGBZ/vEQlOKhODxK2wsAml/v9Rm9Ha/CVTbQ2jVWxUH3HyDqDSRQBfYPlA79vxP2CcFEB1DbNla9TlBAwovSJVy9D0oURPoe8XrJqog=
The values to post to the login action will be:
{ "apikey": "QrCDN6CcXkGOnRiNcZMrpw==", "timestamp": "2018-01-22T13:58:33.871Z", "signature": "iMTchrTU9pMWFDRYQNCnUiD2ekDdCgp0ybN7xzvj9DLtceTFsF/kxzr9q5OnqP0quyt7OGBZ/vEQlOKhODxK2wsAml/v9Rm9Ha/CVTbQ2jVWxUH3HyDqDSRQBfYPlA79vxP2CcFEB1DbNla9TlBAwovSJVy9D0oURPoe8XrJqog=" }
Warning
The error Api key authentication failed. indicates that something is wrong with the request payload that was sent.
This can have multiple causes, but here's an overview of the most common causes:
Wrong API key: Ensure the API key is sent both in the request header ("x-api-key") and in the request payload ("apiKey").
Invalid signature: Ensure the create signature procedure is implemented correctly and the value is passed in the request body "signature" field.
Invalid timestamp: A validation mechanism verifies that the timestamp is still a current/valid timestamp to prevent old payloads from being used.
In short, we validate if the timestamp sent in the request payload is within the range of our server timestamp with an allowed clock drift of 2 minutes both in the past and future.
So make sure the machine you are running on has the clock set correctly and that you are using your payloads within the allotted time.
Send values to the Login action.
Login
POST /{version}/login
x-api-key: QrCDN6CcXkGOnRiNcZMrpw==
Host:
For Direct selling API: https://api.staging-enviso.io/directsellingapi
For Reselling API: https://api.staging-enviso.io/resellingapi
For Payment API: https://api.staging-enviso.io/paymentapi
For Scanning API:https://api.staging-enviso.io/scanningapi
For Webhook API:https://api.staging-enviso.io/webhookapi
For eLoxx API:https://api.staging-enviso.io/eloxxapi
Content-Type: application/json
Cache-Control: no-cache
{ "apikey": "QrCDN6CcXkGOnRiNcZMrpw==", "timestamp": "2018-01-22T13:58:33.871Z", "signature": "iMTchrTU9pMWFDRYQNCnUiD2ekDdCgp0ybN7xzvj9DLtceTFsF/kxzr9q5OnqP0quyt7OGBZ/vEQlOKhODxK2wsAml/v9Rm9Ha/CVTbQ2jVWxUH3HyDqDSRQBfYPlA79vxP2CcFEB1DbNla9TlBAwovSJVy9D0oURPoe8XrJqog=" }